A CEO's perspective on how Chief People Officers can meaningfully influence leaders at the highest levels of an organization
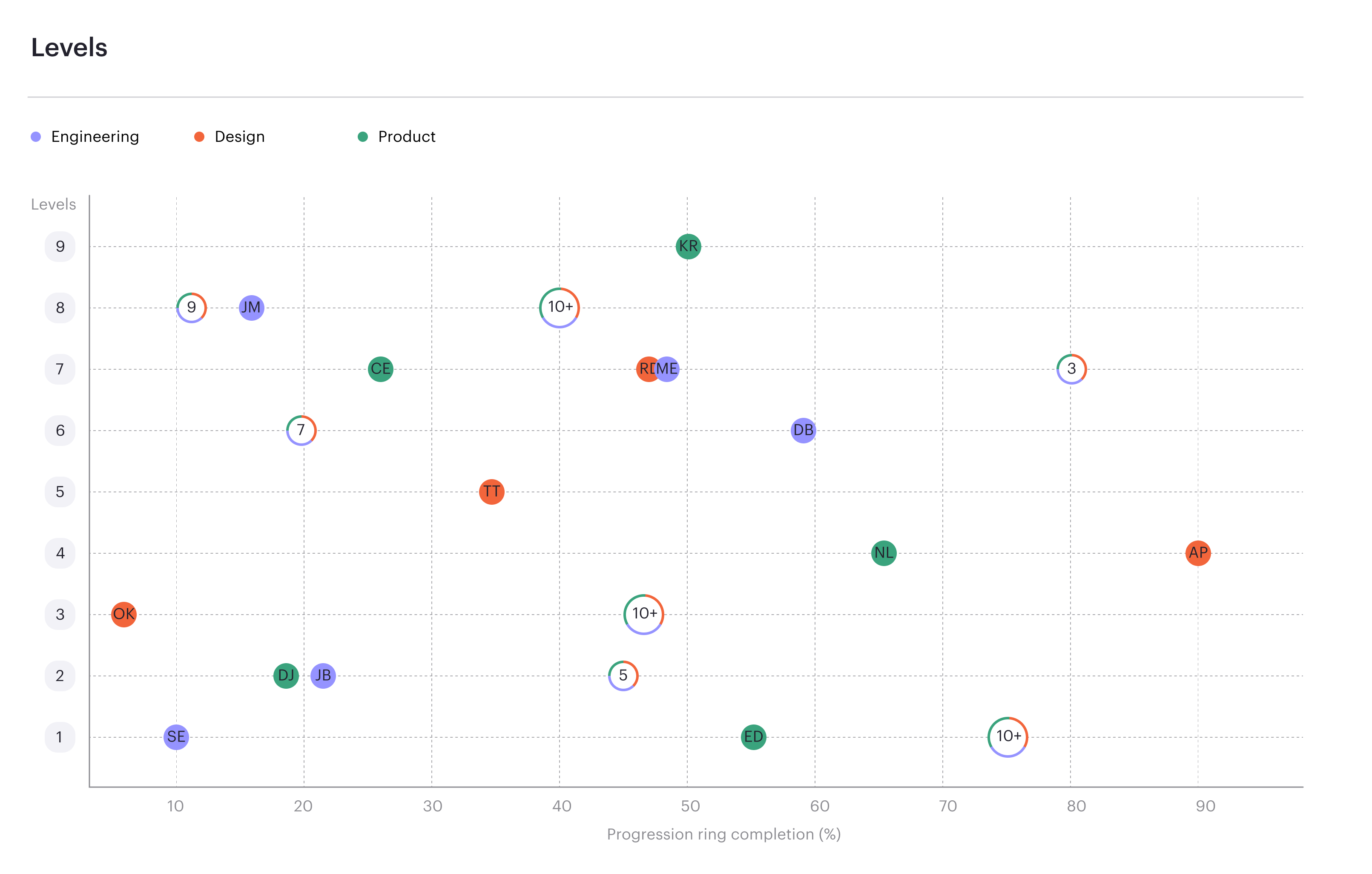
Read moreContinuous progression drives performance.
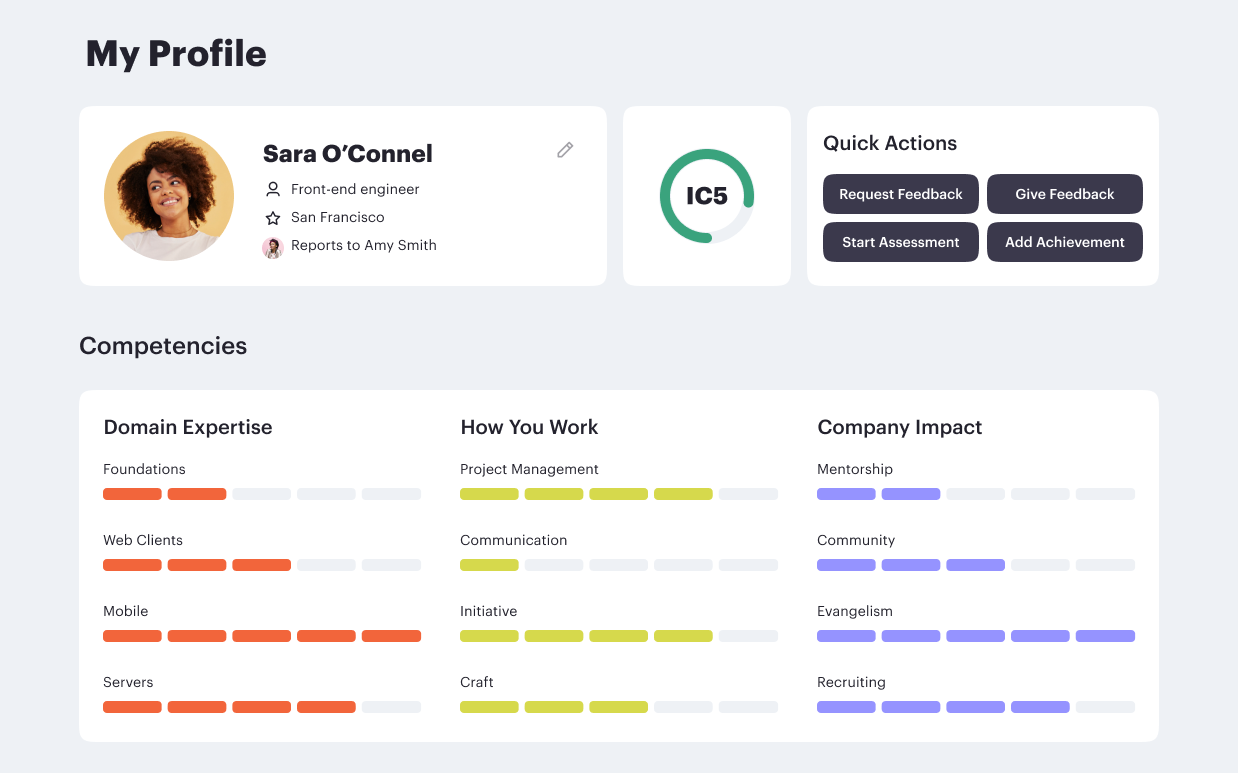
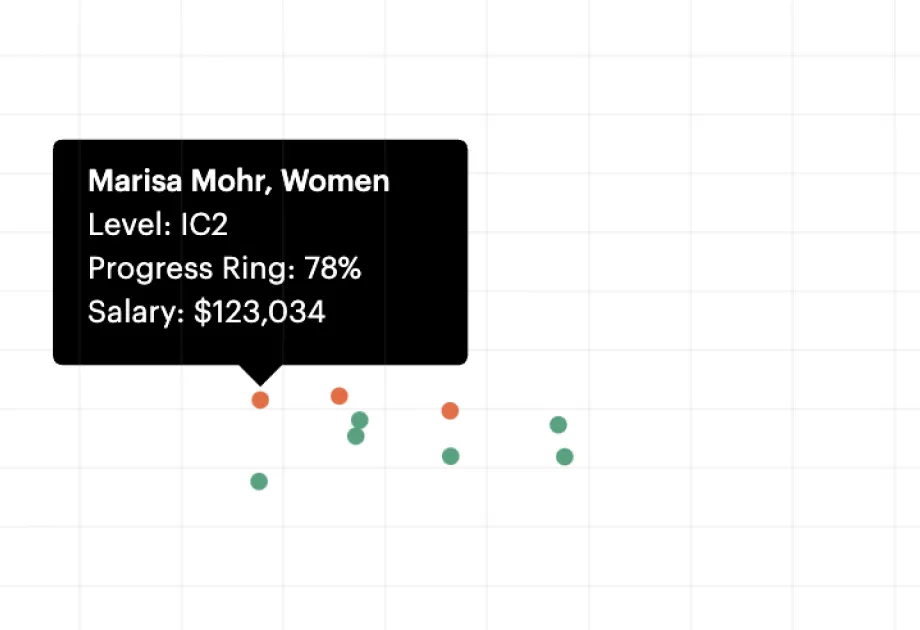
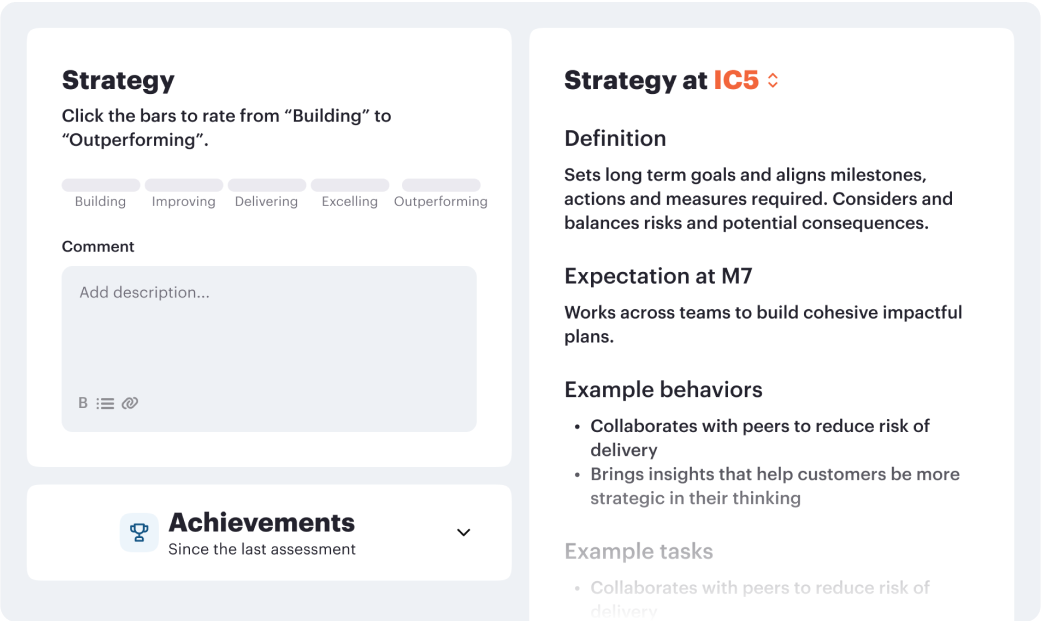
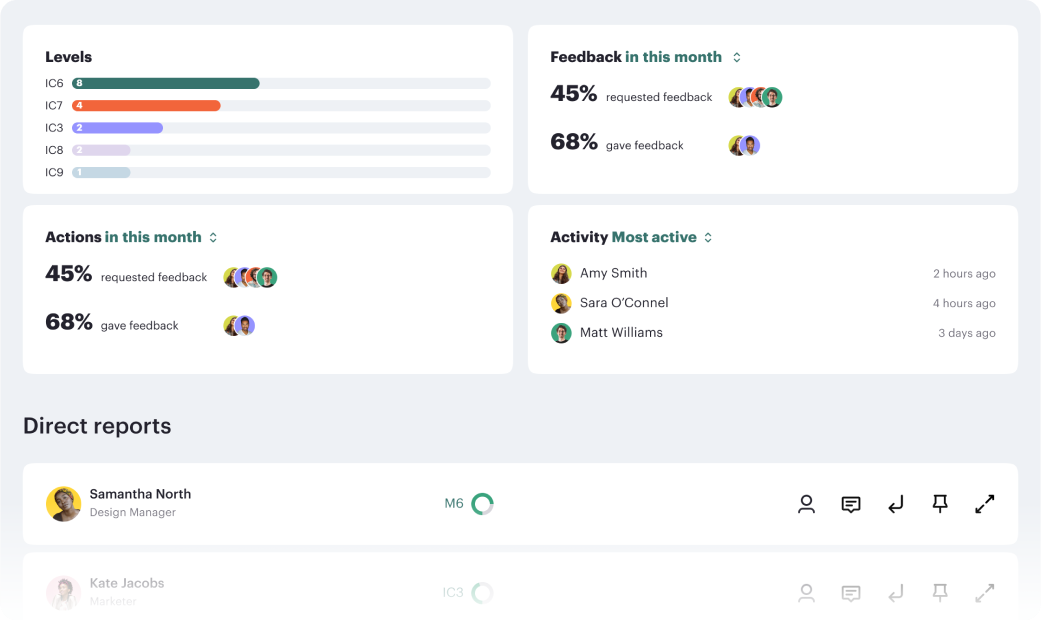
Career frameworks, feedback and goals to structure, measure and accelerate business impact.
Request demo














%201.webp)